SHA1:
LM modules:
- b86935c4539901cdec9081d8a8ca915903adaff1
- ce4b3c92a96137e6215a5e2f5fd28a672eddaaab
- 51a4ca78ebb0649721ae472290bea7bfe983d727
- bf4d9e25fc210a1d9809aebb03b30748dd588d08
- 8a0d58472f6166ade0ae677bab7940fe38d66d35
- 979fb376d6adc65473c4f51ad1cc36e3612a1e73
- 4df58ab26f0fc8ec2d1513611ca2b852e7107096
- 2a809d37be5aa0655f5cc997eb62683e1b45da17
- f73022a4801e06d675e5c3011060242af7b949ad
- 688ccbca8b2918a161917031e21b6810c59eeab0
- c22f0fb01c6d47957732a8b0f5ef0f7d4e614c79
- 41bf0d5612ba5bc9a05e9d94df0f841b159264a0
- 1cc1b97f8f9bb7c4f435ef1316e08e5331b4331b
- a1f2535576116d93b62d7f5fc6e30e66e0e0a216
- ac094b239851eaf2e9fd309285c0996fb33771a8
- 8e3c4eb04d4cfd8f44c721111c5251d30ac848b6
- d8a5d9c4605b33bd47fedbad5a0da9928de6aa33
- 2889803777e2dfec7684512f45e87248a07d508f
- b14f7af9665ef77af530109a0331f8ca0bd2a167
- 5a88b67d8dfaf1f68308311b808f00e769e39e46
- ba5df105496b0c4df7206d29fa544b7a7a346735
- a358bf8a9ad25f210db44252767a2ef3706c7866
- f1c88267459cfaa46bfee6f8655e07e4d610d999
- d5f8078acb5d144912b3b604a44b8e82c6babc0d
- 3ffef7c0b52493854f982b30ba75380af76d860f
- 1a79092c6468d39a10f805c96ad7f8bf303b7dc8
- f84fc11f79bd2ccd33d37c71e6a5c8f55ecdf3f7
- 3f666ef113a74eddb9bc324829f8b16c45e92213
- ec2e8e9a6f50dbc6766d9af90ef4656c9dfef2f6
- 141f9a40cab04cc4b480323f3c84b7134d9c55f6
- 05eb47f3fb2283f4aaaa842211c3babd20306e70
- cd3e216da075f30f242cba3ca878305ed10ea3e1
- 6c0d96f481a1d9ea3abf54ec76dac5a449ece536
- 689c26a8ede9bb399e010b82877e961bebd3afaa
- 877156682bcb30d2c03bb9be30f8ab641a1abebf
- db149c873e833920614db422eb79b50835832dcd
- cf69e85f6336e06d2a4217dc26297e17035daf03
- 6f955867f4291fc1db9efa20f5133f4de097a2cd
- ea059e4986acb65c60fcc661abbd2ab222e2ad02
- 4d50412dba1f7bb9aea8deddf64f034241b7e1c2
- 432741a58785db6b757e2fb3bde13b13672e3932
- 7a8b07ea81ced0cd408fa46cc21711b6bc412422
- aa2135b4e21b278a42209c4a72dcb27198d76151
- ac7353acc2239ed6feb1704af17b59bc53376020
- 65174284676f1fe905e5db81d3b7911b120085e1
- d6b37e3cf7391216811ce2426c17c489df83e261
- 019f29e23e3183059b60b5b1fd267e9f0197068c
- 3c38f33c224ee7c1c086f890033001815f1afa66
DL modules:
- 4ddec62c8a335ff3a3997ce48819c0d23d92f621
- 0f55ffa6f8299b00e1529efc3d65e401fa4846f4
- 96d213747857265a9b76c26abab1c5c8fcb3f87b
- 274181d2f9c6b8f0e217db23f1d39aa94c161d6e
- 8abbb049bffd679686323160ca4b6a86184550a1
- 9cde845852653339f67667c2408126f02f246949
- 95444c2ccc5fff19145d60f1e817fd682cabe0cd
DM modules:
- 105cc7d967da90ed5ad46a5825c5365296c70fb5
- 59f9c1490f78e202f7a63cc634000cf504ce152d
- d2b876473cc54ca772b304114155ac2781a8e83c
- dface45261d62769cbb2c0a435c3ea0a7ba7425e
- b624c9a0aeacf2d5869e598a0b004f1a5fda9ebe
- 6ab9e1c83276db2d9057a5f5cc6821897af2a83b
- f2b44b7fb39d5628109eb128caebe3c481dd16d2
- 42d965a29b77e8261c9b5a1525933861b4cfd052
- 52e833630b141648e61e56175d371cbe19c1e607
- b3670fe162a461b9e5744ff25041722f7ce1b209
- b936492f17328852ca7adc33c6229a28b4423ecd
- 900edeaa548a935cd2f431be48d1e5cb445c382f
- 956e903ed42e7eadb8cedb3d2a5b216ca7fc8991
- 70e883bdfd576fa6d1f621be3752e651472e1f82
- eebabf60bf9bddf0ee9ef5c453320089ef5f80a7
- a594f6ad9e23b8bd1e07b54b5755f1d042238a42
- a2d51bffa629851734d51823319c9dccf1a5d6c0
- c4f4b1075115ecdb1e906cc15b5545d0e600956f
- 0b303ad8c481dcf039d2cae03c890b3894e7cf92
- 26bb4336be46f6fceb5bb63d67795c5cb13e2f54
- c0053ebd64f09f324b6dfa31264f107acf45b59d
- 70bd08854371e869eaa030dec69f5bed68189edb
- dd400d68bd634fa776a7dc2b1e30414d08393311
- 1de17117a226a1788c6e57fa39ac4f218db2f73d
Linux Trojan written in the script language Lua. First attacks with this Trojan were registered in December 2016. Since then, these malicious programs have been constantly evolving. The Trojan consists of 31 Lua scripts, packed using UPX, packed scripts are written in the end of the packed file between the tags “--block–” and “--block-end–”. The list of scripts in the Trojan:
async.lua
bencode.lua
bfssh.lua
bfssh.lua.old2
bftelnet.lua
btloader.lua
callhome.lua
callhome.lua.old
config.lua
crypto.lua
dht.lua
http.lua
httpproto.lua
main.lua
persist.lua
readme.lua
routing.lua
scanner.lua
server.lua
socks.lua
ssh.lua
ssl.lua
telnet.lua
test.lua
test2.lua
test3.lua
threads.lua
torrent.lua
udp.lua
utils.lua
worm.lua
bfssh.lua
A script that is designed to brute-force attack remote nodes using a special dictionary. The following values are used for generation of combinations:
{"admin","admin"},
{"root","root"},
{"adm","adm"},
{"ubnt","ubnt"},
{"root",""},
{"admin",""},
{"adm",""},
{"user","user"},
{"pi","pi"},The script contains a list of subnets, which avoid the attack:
"0.0.0.0/8",
"10.0.0.0/8",
"100.64.0.0/10",
"127.0.0.0/8",
"169.254.0.0/16",
"172.16.0.0/12",
"192.0.0.0/24",
"192.0.2.0/24",
"192.88.99.0/24",
"192.168.0.0/16",
"198.18.0.0/15",
"198.51.100.0/24",
"203.0.113.0/24",
"224.0.0.0/4",
"255.255.255.255/32",
The script checks the architecture of the attacked device by the file name “/bin/ls” of the directed device. The Trojan infects devices possessing the following architectures: Intel x86 (and Intel x86_64), MIPS, MIPSEL, Power PC, ARM, SPARC, SH4, and M68k.
From the very first known versions of the Trojan, it makes attempts to detect honeypots with the command "echo -en":
When downloaded on the attacked device of appropriate architecture, it is saved to file “/tmp/drop”:
When the attack is carried on via the SSH protocol, the Trojan is loaded to the file /tmp/drop and then launched.
Information on compromised devices is saved in the text file ssh.txt in the following format:
ip;port;user;password;arch
Where:
- ip—IP address of the hacked device;
- port—connection port;
- user—user name;
- password—password;
- arch—device architecture.
- bftelnet.lua
bftelnet.lua
This script operates the same way as bfssh.lua. The following values are used for generation of combinations of logins and passwords:
local accounts={
{"admin","admin"},
{"root","root"},
{"adm","adm"},
{"acer","acer"},
{"user","user"},
{"security","security"}
}In the course of an attack via the Telnet protocol, the compromised device is loaded with a small DL module, which is used to download the actual Trojan. Information on compromised devices is saved in the text file ssh.txt.
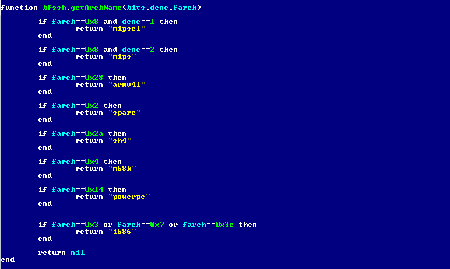
server.lua
HTTP server of the Trojan is implemented in this script. The port is indicated in the configuration file of the malicious program: port 8888 is used by default. The HTTP server can execute the following commands:
- /upload—save and execute file. When launched, the file signature is checked with the public key stored in the configuration.
- /info—returns information on the Trojan in the JSON format, including versions of Lua and backdoor, and data on the device architecture and the Trojan module. This function is disabled in the version detected back in May 2017.
- For the rest of requests, the Trojan determines the basename of the request (file name) and checks its availability in a work folder of the Trojan. If the file is present, the Trojan sends it; if else, it returns the 404 error.
httpproto.lua
The script contains functions for operation via the HTTP protocol, including functions for traffic encryption during the transfer of data to the command and control (C&C) server. The packs transferred to and from the C&C server contain the value of the first DWORD with the RC4 key for encryption; the first DWORD in the decrypted information contains CRC23 from data.
The packs received from the C&C server contain not only RC4 and CRC32, but also the signature ed25519 that is checked by the key from the configuration of the Trojan.
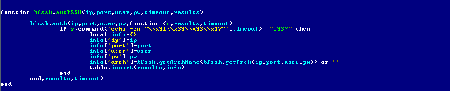
btloader.lua
The script with the functions for operation of the P2P network, in particular, reception of files of configuration and modules via the Bittorent DHT protocol. All configuration files and update lists are supplied with the signature for verification procedure.
In order to obtain updates, the script addresses the P2P network, generates info_hash in the format of sha1('%s%s' % (pub_key, name)), where pub_key is the public key from the Trojan configuration file, name—configuration file name (server, update, script). The received data has the following structure:
{
'k': '\xc6Z7\xab\xd4\xae\x10\xca\xcf\xc7f\x9d\xf4Vx\x19f\xc6\x86$@\xe0\x19!\xef\xf7\xdd\x9b\xe9,s\xca',
'sig': '\xb51\xdai\xb9\xc1\xd9\xc6k8h\xf5\xe4j\x889\xdf\xa9XW@\x08T\x0c328_\x99\xac\xeeqt{\xff[F^\xdfT\x87\xa8X\xde\x9d\xff\xabg\xc0\x16_\x83\xa6\xd7\xc0\xb0\xfd\x1d\xdc~\xf0*\xb5\x0c',
'seq': 1493655967,
'v': '176.***.***.145:8080\n'
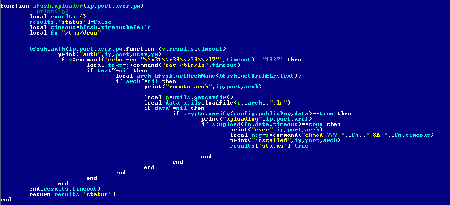
}where k—public key, sig—signature, seq—timestamp of creation/signing of data, v—payload. If the value of seq is higher than the one of the available configuration file, it will be replaced with the configuration file obtained from the network.
Once the Trojan obtains new configuration files, it launches two threads, one for the update configuration and another—for the script configuration. These threads pick configuration files and extract from them pairs “name-hash”. Then the P2P network receives a request for the search of peers that have info_hash that is generated as sha1('%s%s%s' % (name, seq, data)), where name is the configuration name (update/script), seq—its timestamp, and data—configuration data. All detected peers are considered to be sharing servers. The Trojan sequentially downloads a file from each of the servers and checks its hash for matches with the searched one. For all files, except scripts, a digital signature is also checked.
banner.lua
The script contains the following text:
ВСЁ ИДЁТ ПО ПЛАНУ
А при коммунизме всё будет за**ись
Он наступит скоро — надо только подождать
Там всё будет бесплатно,там всё будет в кайф
Там наверное вощще не надо будет (умирать)
Я проснулся среди ночи и понял, что -
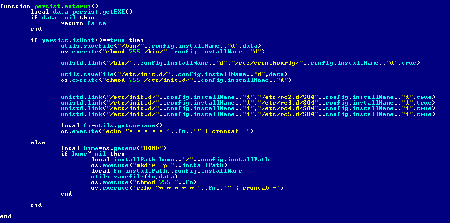
ВСЁ ИДЁТ ПО ПЛАНУpersist.lua
The script contains functions for installation of the Trojan to the autorun using Cron or a system service. To do that, the malicious program creates symlinks to the copy of its executable file:
socks.lua
Creates the SOCKS5 proxy server on the port indicated in the configuration file.
worm.lua
The script that is supposedly designed for the self-update of the Trojan under the condition of inactive P2P connection. Scans subnets in search of devices infected with its own copies (checks ip:8888/info) and saves all its LM scripts on these devices upon request (ip:8888/upload).
DL module
This module is installed on a device hacked via the Telnet protocol to the file “/tmp/srv” and launched with the stdout redirection to the file /tmp/drop. The Trojan connects to the port that interacts with the DL module and downloads its copy to the compromised device. Then it connects to the compromised device and installs access privileges for the file /tmp/drop, after that it runs its own copy.
DM module
Improved version of the DL module. It is installed in the folder “/tmp/dwl” on the compromised device and launched with the stdout redirection to a file. It receives an argument with a link to the file and downloads this file to stdout.
Versions
The following versions of the Trojan are currently known:
| Build date | Known modules | Features of |
|---|---|---|
| 2016-11-27 | i686.dl, mips.dl, mipsel.dl | |
| 2016-12-14 | i686.dl, mips.dl, mipsel.dl, armv4l.dl | |
| 2017-02-06 | mipsel.lm | First known version of the LM module. |
| 2017-02-12 | i686.lm, mips.lm, mipsel.lm, armv4l.lm, powerpc.lm | The worm.lua script is removed. |
| 2017-02-19 | i686.lm, mips.lm, mipsel.lm, armv4l.lm, powerpc.lm |
|
| 2017-02-28 | i686.lm, mips.lm, mipsel.lm, armv4l.lm, powerpc.lm | The module for hacking via the SSH protocol and P2P module were added again. |
| 2017-03-08 | i686.lm |
|
| 2017-03-12 | i686.lm, mips.lm, mipsel.lm, armv4l.lm |
|
| 2017-04-10 | i686.dm, mips.dm, mipsel.dm, armv4l.dm, powerpc.dm, sh4.dm, mipsel.lm, armv4l.lm, powerpc,lm |
|
| 2017-04-11 | i686.lm, mips.lm, mipsel.lm, armv4l.lm | List login:password was significantly expanded in order to hack nodes via the SSH protocol. |
| 2017-04-15 | i686.dm, mips.dm, mipsel.dm, armv4l.dm, powerpc.dm, sh4.dm, i686.lm, mips.lm, mipsel.lm, armv4l.lm, powerpc.lm, sh4.lm | Fixed an error in the bftelnet.lua script. |
| 2017-04-29 | i686.dm, mips.dm, mipsel.dm, armv4l.dm, powerpc.dm, sh4.dm, i686.lm, mips.lm, mipsel.lm, armv4l.lm, powerpc.lm, sh4.lm |
|
| 2017-05-01 | i686.dm, mips.dm, mipsel.dm, armv4l.dm, powerpc.dm, sh4.dm, i686.lm, mips.lm, mipsel.lm, armv4l.lm, powerpc.lm, sh4.lm | Changed the address of the command and control server. |